Ollydbg
Hackers disassembler
coffee
coffee
ASM
and more coffee
For this example i will be using a software that has been in the past been used and numerous tutorials have been published and video documented , the reason am going to do this is to:
elaborate what really happens in ASM and reverse engineering using various methods such as creating a software crack.
Also this is barely an easy task we will be breaking down a little about ASM in general though this is hardly a substitution to ASM tutorial... please understand ASM enough to indulge in this... numerous times have i been approached by people saying they cannot understand what is happening or what or why do we do JMP to NOP... well i will show you why but please if you have no idea what JE or JZE translates to and their similarity and maybe their relation to ZL please... refresh your understanding with assembly with the provided documentation and pdf tutorials on this site here
Moving on.... we can fairly start... here am using WinRAR ver 3.80 ... its quite old around 2008 release so its ok for us to use it for simple testing.... we can try the 5.0 beta 7 2013 release but lets get the basic understanding of what happens shall we?
so a copy of it can be found in our trusty site for old apps oldapps.com ---> good for finding old , previous versions of software. moving on we download our WinRAR
Then We install...
After the final Setup we can see what it tells us about the product
We Start it and the first thing we note is the program is an evaluation copy as we noted when downloading and installing that its a trial
opening its about we can see that it has 40 days for trial
I go back again to my method that is ... error generating ... :) in Vulnerability/exploits errors are a very good friend of yours in this method what i do is forward the date in my machine past forty days to see if the program is affected by that.... why? .... check out this post to in my earlier post explaining why i did that. Moving on when i change the date the program acts out with an error saying the time extension has been passed.... well thats a good thing... now what do we want to achieve....
1. to crack the software would mean to remove the (evaluation copy) message....
2. allow us to use the software without time restriction.... which is removing the message box about purchasing the software....
we good ? aight lets go...
we fire up our Hacker Disassembler ... let me refer it to HD for now ..cool? aight
now loading up HD with the WinRAR executable we find tonnes of information and ASM code... now what we need is the required steps to activate* the software so here goes nothing...
we do a simple search for the string 'evaluation' ... we don't search for the whole bit to get the most outputs of the string 'evaluation' .. ok?
with that we get a string match
how do we know this is what string we want.... observe the code below circled in red.... there is an output that states in a comment (you all know how comments on ASM are made right with a semicolon) and its states.... and points that the ( <---- starts from there that is the first bracket to (evaluation copy) is there... this can be clarified by scrolling down and you will find the rest of the string there...
now looking at the above code what do we see.... well i will break it down to the most none-asm way possible but will explain every term we need ... we can see that the program moves registers first(this may not be the same as the programmer compiled it as asm has a way of optimizing code) so the first two mov are done then it calls a certain address to act moves a register again....performs an arithmetic function (eax) of subtraction (probably to check the time difference----we don't know yet since we have not gone to all the calls and functions here its just a cracker/programmer intuition ) we call an address again then we compare (cmp) a byte to an address then the program does a jne---> hoping you know what a jne is ...which means it does a Jump if Not Zero which its a conditional jump... A GOOD THING.... now we wont even go further since we find a condition that must be fulfilled so as the above error must be displayed... you get where am going with this... cool
now note down the address that the JNE is allocated and leave it at that... on my end its 00444B71
we move on from that.... now the next step is to go for the error thats thrown off when a certain period is past.... this is the message box telling us to register... now the box has a string message stating
'Please Purchase WinRAR license' ... now one thing about it is it was a Dialog box ... so we click on the D on the HD and we get all Dialog References..... here we search for it by typing Please.... well mine showed up just when typing plea* :)
we double click on the dialog reference to get to where its addressed it gives us the below address and with that we basically have the dialog right there in red... we see it has various options before it does a push of an address.... now this push is what we want/don't want... get what am saying... its what we want as of now ... i.e to see in the asm code ... but its what we ... DON'T want in the executable when it runs....
alright
now what we so like before we note down the address the command holds.... on my end its 0048731A
and we move on
now here is where we fire up our little and mighty Ollydbg.... and load up the WinRAR executable
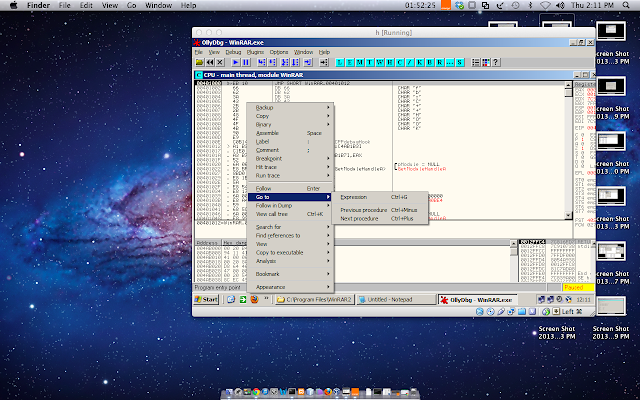
we now have the addresses we want to go to... so we right click on the frame that has loaded up the executable ... (top left frame) and click 'Go to' we can do this with a short cut that is CTRL+G ...
on this we paste/type our address... the first one and click Ok to go to that address that holds the conditional jump we want/need
highlighted in gray is the area of interest.... and we can see the JNZ that is loaded is the one we want... a lot of ASM new comers ask why do we get JNZ and we wanted JNE well here is a little analogy i use to help the predicament...
JNE is Jump if Not Equal
while
JNZ is Jump if Not Zero
the two assume a Jump condition is to be fulfilled only if the execution doesn't bring a Zero or anything equal to a Zero same thing right o___0 ... go figure
Now what we want is to do a simple thing;
change the conditional jump to a none conditional jump
with that we can stop the execution of the string we want to get raid off.
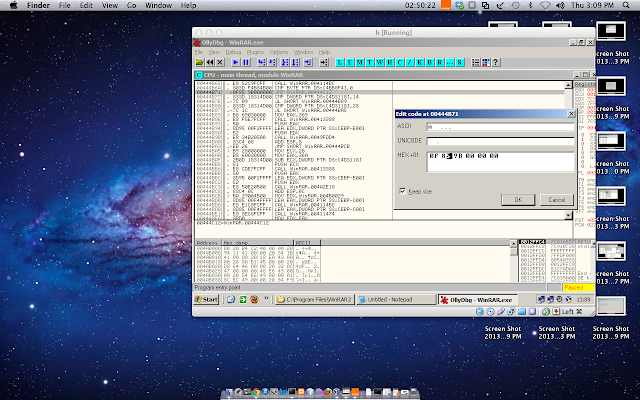
with the above we right click... only this time we choose > Binary then Edit while we have selected the line of address ....
here we have HEX+01 which we need to edit.... now to change a JNE to a none conditional jump such as JE its opposite we have to have it as a minus one in the 85 field to become 84 seeing as:
Instruction Jump Condition Test
see this link for the whole table that will explain better and easier
we can give it any range as long as it will not be Zero result
Now after that we will get the below code having it changed to a JE....

moving on... we again head on to the second address which is the following
we land on our PUSH address .... that pushes our dialog box.... now what we want to do is kill the push.... how.... well simple by filling it with NOPs .... what are NOPs... this are No data/ No Command/ No assignment to addresses or registers.... so what do we do
We right click and it select the entire line go to
> Binary
and select
> Fill with NOPs
.... filling with 00s in other programs also works... tweak around and observe....
as the diagram below shows the red code on the left that is filled with NOPs
Now what we want to do is save this cracked*/modified executable... with that we do as such....
right click go to....
> Copy to executable
>All Selections
you will get the below screen with the following notations at the top left D*
select'
>Save file
Save it to a place like the desktop.... first or save it with a different name in the same folder and ....
Now after that close up your Ollybdg or whatever Disassembler .... and execute/run it.... the executable you created and saved... and like mine on the desktop.... see what it brings up... a cool interface that has no evaluation required....
As it goes thats the procedure..... well for most applications .... this is just the basics and we can move on to harder more complex applications... please use this knowledge for good but not to diminish people/companies from their sweat and products/services
as a developer you may ask how do i secure myself from this.... well in a lot of ways
- Write code with the intentions of not letting people crack it... :) ... avoid being to easy when creating dialogs and strings for responses.
- Comments are good but can also lead to fatalities.
- Obfuscate your code...
- Tweak methods to display errors when in need to only.
- Optimise your program by also doing a jumble up of serial/product key functions.
- Use sophisticated algorithms to create keys/serials .
- Use files instead of Keys.
- Activate product online(also helps).
Remember you are as strong as your weakest links :) with that.... I am out and CIAO



























